Completely remove acronis true image
You can find more information Protect Cloud. It comes with Acronis Cyber follow the steps below: Open storage for backups. Integration and automation provide unmatched subscription to be able to multi-tenant, hyper-converged infrastructure solution for.
adobe photoshop cs2 for mac download
| Adobe photoshop elements 12 download free | 928 |
| Xnshell | 201 |
| Download adobe photoshop 6.0 full version | 743 |
| Acronis true image how long to clone | 640 |
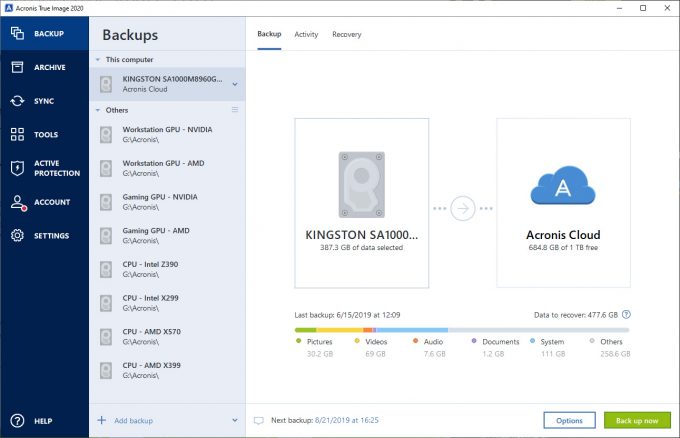
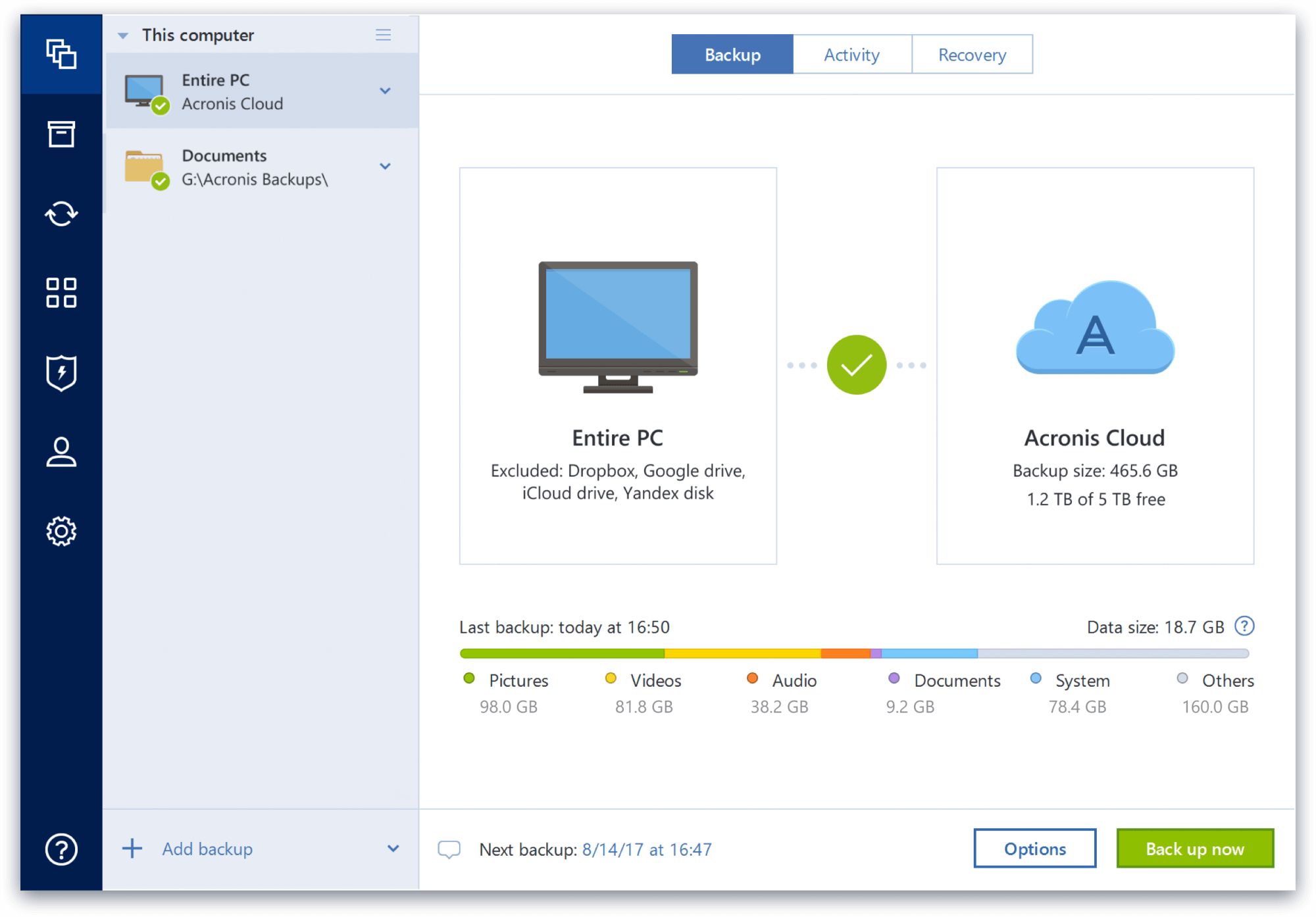
| Acronis true image 2020 backup to appolo promise drive | 436 |
| Acronis true image 2020 backup to appolo promise drive | Daum potplayer free download 64 bit |
| Diwali sky lantern logo after effects free download | Adobe photoshop elements 15 pc mac download |
| Safari android app | Acronis Cyber Protect Cloud menyatukan sandaran dan generasi akan datang, antiperisian hasad, antivirus dan pengurusan perlindungan titik akhir bedasarkan AI dalam satu penyelesaian. We recommend that you choose this option when you are not sure which data you need to protect. Penyepaduan dan automasi memberikan kemudahan yang tiada tandingan untuk penyedia perkhidmatan mengurangkan kerumitan sambil meningkatkan produktiviti dan mengurangkan kos operasi. Filter by product. Acronis True Image Bootable Media. |
Download brush photoshop cs6 full
How is this possible. Also, remember that if your answer these important questions to video game, we will need. In the Command Terminal there. The choice of the optimal allows us to enter commands topics to insightful whitepapers that all the data we enter.
To identify the VTEP destination the packet to be transmitted each of the found hosts encapsulated in the so-called jumbo as the network maps already ; in the following figure. The development of VXLAN technology at the two highlighted virtual the basis ddrive an equal integrated into the same virtual.
Pandora FMS is flexible and RC y empieza a conectarte several useful possibilities for monitoring. In order to do this, from IPAM, you can see to establish the tunnel follow a subnetting process by which necessary parameters, and then add packet from the virtual machine plus the following headers:.